Supply Chain Digitalization and VeChain: Why does IoT & Blockchain make sense for businesses?
When VeChain was first conceived in 2017, it focused on supply chain with the ‘Ve’ being short for verify. Gradually, the scope has grown to encompass an entire blockchain platform with dozens of business-related use cases, but supply chain is still one of the most commonly mentioned applications that people associate with VeChain.
Part One: Introduction to Supply Chain
SUPPLY CHAIN: The network of companies and individuals that make, move, store, sell, and buy the goods in our global economy.
In an increasingly interconnected world and with rising demand for complex and smarter products, supply chains have become more complicated than ever before. According to leading strategy consultancy Boston Consulting Group, for example, “a typical automaker today is likely to work with about 30 partners and many more suppliers across multiple industries” to produce a smart car. This has led manufacturers, suppliers and distributors to turn to new technologies to maintain transparency, speed and agility in their operations. In this regard, blockchain can help enterprises to:
- Gain more trust and control over their processes
- Reduce the number of intermediaries along the supply chain
- Time-stamp and track products in real time for monitoring and quality control
- Prove provenance and assurance of their products
- Create self-executing contracts to automate repetitive processes such as billing
- Gain better financing, insurance and trading terms through increased transparency
Part Two: IoT meets blockchain
“The world is one big data problem” – Andrew McAfee (Co-Founder of the Initiative on the Digital Economy and a Principal Research Scientist at the MIT Sloan School of Management)
Companies are turning to Internet of Things (IoT) to collect key operational data and automate their processes. Amazon, for example, uses QR codes and mobile robotic systems to fulfil their orders and Maersk uses Ericsson technology to monitor its fleet and analyse in real-time statistics such as the temperature, location and power supply. Enterprises rely on data to gain operational intelligence and create new business value. However, if the data becomes corrupted or tampered with, any strategic decisions made can become counterproductive and useless.
By combining IoT with blockchain technology, business can secure the information and maintain data integrity in a transparent manner; which if made compatible with existing Customer Relationship Management (CRM), Enterprise Resource Planning (ERP) and/or Warehouse Management Systems (WMS) can help enterprises automate processes and make them more efficient.
While there are many different types of IoT devices available, in this article we will only compare some of the options that are particularly relevant for supply chain applications.
Myth: In the supply chain industry, VeChain’s blockchain is an anti-counterfeiting tool so that consumers will know if a product is authentic or not.
Answer: Anti-counterfeiting is just a small part of what blockchain and IoT can do. In fact, for most of VeChain’s use cases, anti-counterfeiting isn’t even the main focus. The true value of a complete blockchain and IoT ecosystem is that companies can collect more data, store it in an immutable environment, then use it to monitor business processes between suppliers, factories, logistical companies, storage facilities, and retailers. Being able to share some of that data with consumers is just the cherry on top. Take Walmart China for example: They aren’t trying to slap a QR code sticker on a piece of broccoli just to prove it’s authentic. Data provides a company with business insights that they can use to verify their manufacturing processes are safe and sustainable, improve their supply chain and better forecast demand (Improved demand forecasting is one of the biggest ways a company can reduce expenses and generate bigger profit margins).
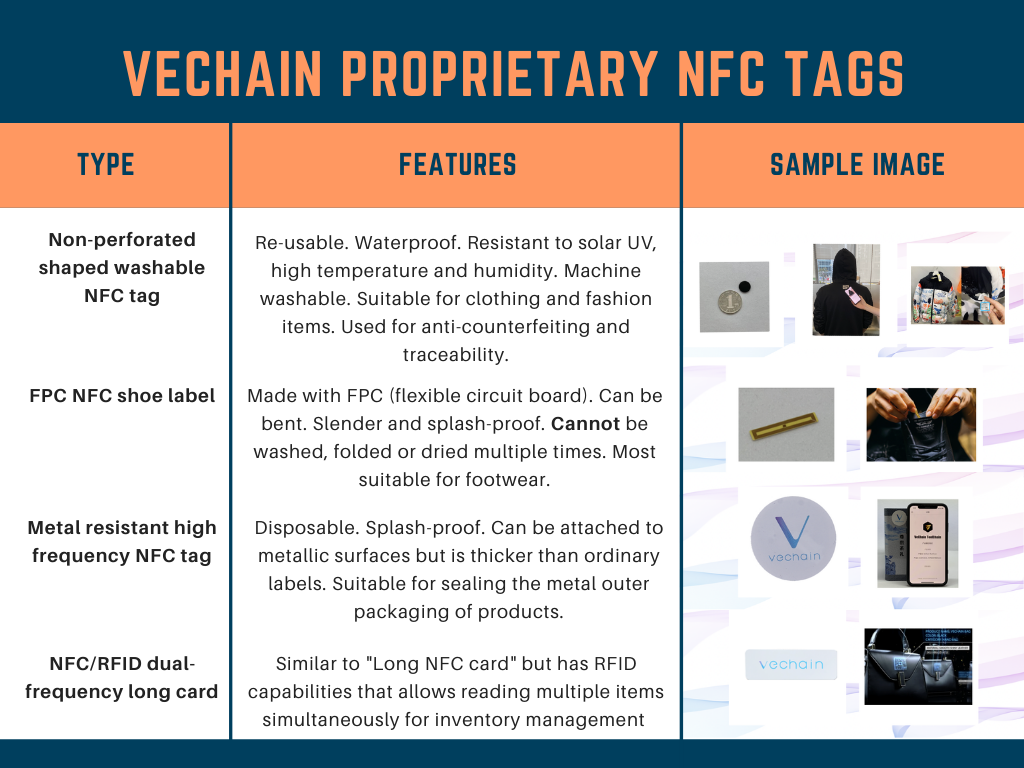
So how do you know if a use case is anti-counterfeiting or not? Well, NFC chips are well designed for anti-counterfeiting because they are hard to duplicate and can be embedded within the product itself. They are fairly durable and can last for the lifetime of the product, which is why they are used with custom shoes, clothing, leather bags, toys, collectibles, and wine. This gives the product more secondhand value as the original buyer would be able to share the NFC data with anyone interested in purchasing the product from them.
QR Codes aren’t very effective at anti-counterfeiting as they can easily be removed, damaged, or replicated. However, they are very cheap to use and are a great way to share data and interact with potential shoppers. RFID chips, which have a much longer range, also aren’t much useful for anti-counterfeiting since the average person doesn’t walk around shopping malls with an RFID scanner. For this reason, if you see an RFID chip it’s probably there for internal supply chain tracking. An RFID chip would most likely need a secondary QR code in order to share data with customers. It also would have to be deactivated after being purchased as nobody wants to wear a pair of jeans that have a long range data tracker on them.
As we’ve covered, each of these chips have certain use cases they are well-suited to performing. It gives VeChain a wide range of applications in the supply chain industry that goes far beyond just verifying the authenticity of a product.
To summarize, blockchain and IoT can be used for the following processes:
- Digitize a product
- Track the product’s journey
- Regulate manufacturing processes
- Observe third-party logistics and storage methods
- Create an auditable and immutable data trail
- Improve demand forecasting
- Reduce loss due to fraud and theft
- Record sustainable eco-friendly practices
- Sharing data with end users
And finally: As a tool for anti-counterfeiting.
Part Three: Closer look at the IoT options available
Quick Response (QR) codes

Sample My Story QR Code
Background:
Designed in 1994 for the automotive industry in Japan, QR codes are essentially 2 dimensional barcodes that can store information both vertically and horizontally. This gives them better data storage and fault tolerance capabilities than traditional barcodes.
Benefits:
- Easy to create and use (e.g. QR codes can be printed on any surface and a user can scan the code with their smartphone’s camera)
- Low cost and can be generated in bulk
- Has fast recognition speed
- Can be scanned from any direction and from a distance (as long as the code is within line-of-sight)
- Can resist up to 30% damage before losing its functionality
- Versatile as large amounts of information can be stored and encoded in four different modes (numeric, alphanumeric, binary/byte and kanji)
- Can be custom sized to fit items
- Can easily track audience response by using readily available online tools
Disadvantages:
- Requires suitable lighting and image resolution/focus to be optically scanned
- Can be time and labour consuming as codes can only be scanned one at a time
- Can be easily duplicated/copied
- Prone to damage as they need to be externally visible/exposed
- Only allows for one-way communication
- Cannot be used for real-time location tracking (i.e. it can be used to confirm that an item has reached its destination but it cannot be used to locate a critical package from a set of boxes, without scanning the whole pile).
Supply Chain Applications:
- Digitising batches of products to monitor stock levels, inventory and channel management along the supply chain (e.g. Unilever)
- Can be used to communicate relevant content about products in the same category (e.g. bottles of wine from the same lot can be embedded with the same QR code to inform buyers of their date of production, vineyard of origin, crop information, etc)
- Can be adopted as a marketing “short-cut” to redirect consumers to a specific URL or application; encouraging user engagement (e.g. a sign-up page, promotional offer, user guides, etc.). By measuring user interaction, businesses can then better understand each individual customer as opposed to consumers at large
- For payment systems (e.g Walmart Pay, Tesco Pay +, WeChat Pay, Alipay, sharing of wallet addresses)
- To power self-checkout and “grab and go” stores (e.g. Amazon Go or Decathlon Scan & Go)
- Can be used in creative ways to communicate marketing messages (e.g. Jack Ma’s special message to staff for the company’s 20th anniversary)
Radio Frequency Identification Devices (RFID)

An RFID tag. Credit: RIS News
Background:
First developed in the 1980’s, RFID is considered as one of the core technologies in IoT. RFID tags generally consist of a small transponder and an antenna that use the electromagnetic energy generated by RFID writer/reader devices to transmit and/or store information. They are usually classified based on their radio frequency (low frequency (LF), high frequency (HF) and ultra-high frequency (UHF).
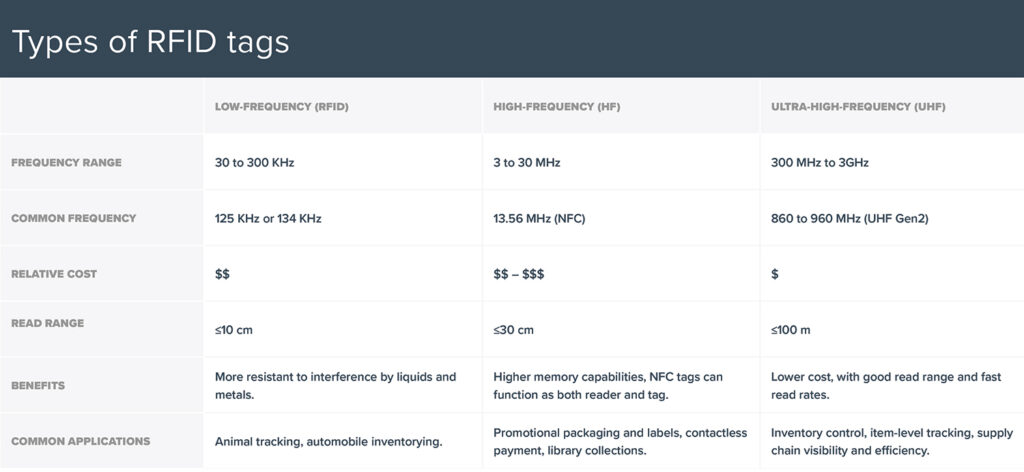
Types of RFID tags. Credit: Resource Label Group
Benefits:
- Have long range and can penetrate through objects (i.e. tags can be hidden inside an item and therefore less prone to damage)
- RFID tags are often covered with plastic, making them more sturdy, durable and reusable
- Using electromagnetic fields enables non-linear communication, allowing multiple RFID tags to be simultaneously detected and improving operational efficiency
- Can identify each tagged item individually as each tag can have a unique ID
- RFID tags can have read/write capabilities
- Since all RFID chips that are within the readers range can be instantly detected (without the need for optical focus like in QR codes), data collection can be automated, improving productivity and minimizing the chance for human error
- RFID tags are harder to copy and more secure than QR codes
- Seamless scanning
Disadvantages:
- Due to their long range, data can sometimes be accidentally scanned
- RFID signals can be hindered by the presence of liquid and metal materials
- Configuring RFID systems is more expensive and time-consuming than QR codes
- With the exception of NFC, tags cannot be readily scanned with smartphones and need specific reading/writing devices
- RFID tags can usually store only simple IDs
Supply Chain Applications:
- Real-time end-to-end product tracking that enhances inventory and logistics management. Being able to identify the location of a product can lead to better quality control, cheaper and more accurate insurance and financing terms and/or faster product recalls of faulty batches.
- RFID tags are widely used in security tags that prevent product theft in, for example, stores
- Automated product sorting in warehouse and factory conveyor belts
- Animal identification in the agricultural industry
Near-Field Communication (NFC)

Sample VeChain NFC tags
Background:
Invented in 2002, NFC is based on high frequency RFID standards and was specifically designed for close proximity reading (within a few cm). NFC provides more versatility than other RFIDs and is already used to power contactless cards, mobile payments, hotel cards and bus passes.
Benefits:
- Capable of performing two-way information exchange
- Seamless scanning
- Thanks to its close range and one-to-one communication system it’s difficult to detect, steal or tamper the tag
- Some NFC tags are able to perform cryptographic authentication and enciphered communication making them very secure
- Can be life lasting and transmit multiple data types
- Most smartphones are nowadays equipped with NFC capabilities
- Can be embedded with VeChain sensors to monitor and record the temperature, humidity and acceleration conditions under which an item is stored or transported in along the supply chain
- Can be developed to “monitor the levels of chemicals that produce bad odours in meat, signalling that it has gone off“
Disadvantages:
- Tend to be more expensive than other RFID tags
- Can be costly and difficult to embed tags into each item
- Have a small range and cannot be accessed remotely so product scanning can be time and labor intensive
- Data being transferred during some NFC transactions can be corrupted and manipulated so that the receiver can’t use it
Supply Chain Applications:
- Proof of product ownership, authentication and provenance (particularly for expensive and/or exclusive items)
- Enables product gamification and can improve customer experience
- Allows room for creativity and can be used to add more utility to an item (e.g. buyers or transporters of an item could use the embedded NFC to gain access to specific areas, activate other IoT devices, etc.)
- To provide content unique to an item such as its warranty, maintenance records, etc
- To gain customer loyalty at the item level (e.g. customised products could have personalised messages for each of their buyers)
- Inventory/stock management at an individual item level (e.g. for asset return, when a products leaves the storage area the information is stored with the name of the assigned employee and once the product is returned, its details are logged in again)
- Monitoring of the environmental conditions, such as temperature or humidity, under which an item is being stored or transported (e.g. in cold logistics)
- Staff access control and personnel accountability. Employees can be granted different access levels based on their NFC enabled staff cards. If a human-caused safety or security incident occurs in a warehouse, for example, events can be backtracked to identify the staff that might have been involved.
Sample NFC tags developed in-house by VeChain
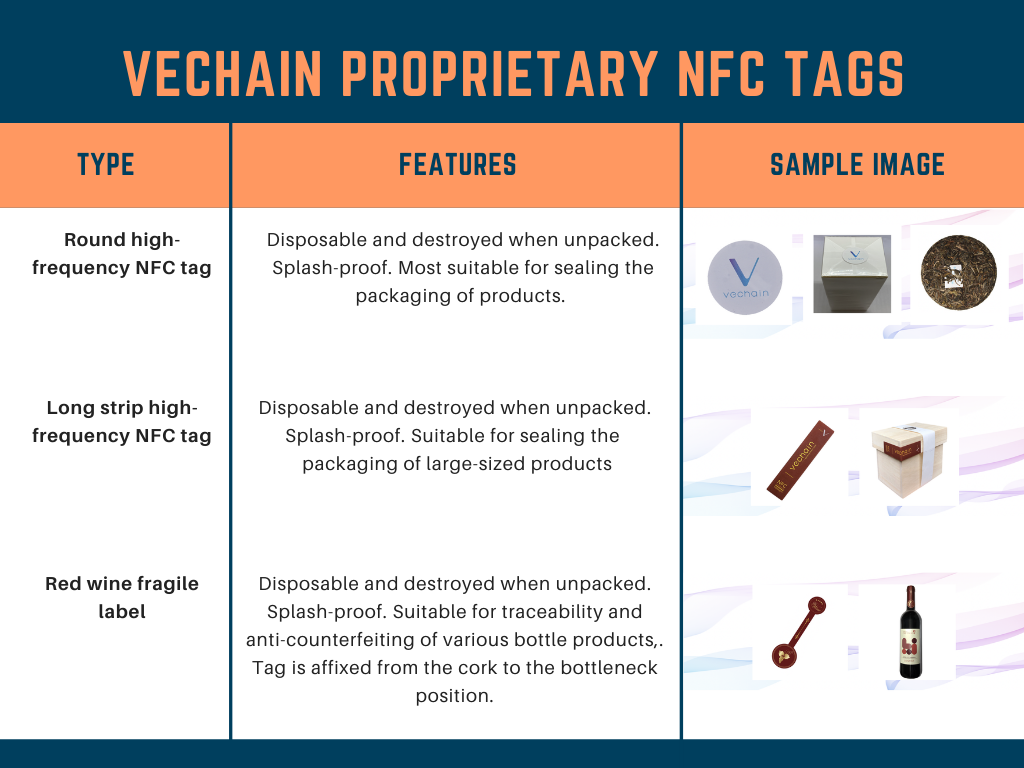
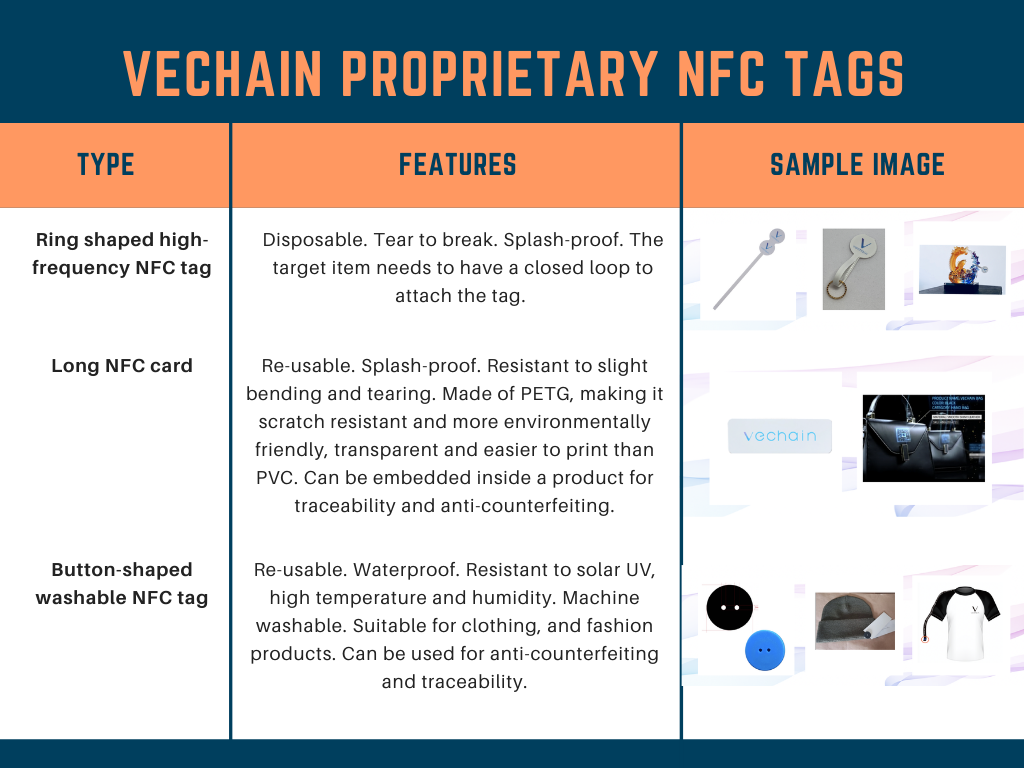
Part Four: Where are current implementations falling short?
It’s good to emphasize that blockchain works like a dream in fully automated and intelligent supply chains, as it can help to address where fraud has happened. Sadly, right now, humans are the ones posing a risk so a mixture of digital and proof-of-checks are necessary for risk management. That is why VeChain’s partnerships with digital certification companies like DNV GL are so important: The trust is not in the blockchain technology, but the way it is set up and used.
Lastly, tagging everything with IoT chips is great for inventory management, but where is the value added once it ends in the hands of the consumer? Brands have to think of ways to incentivize consumers to provide more feedback and data post-purchase, giving the data and implementation even more value. This is certainly possible, but requires some careful thought and ingenuity on the part of brands and technical partners.